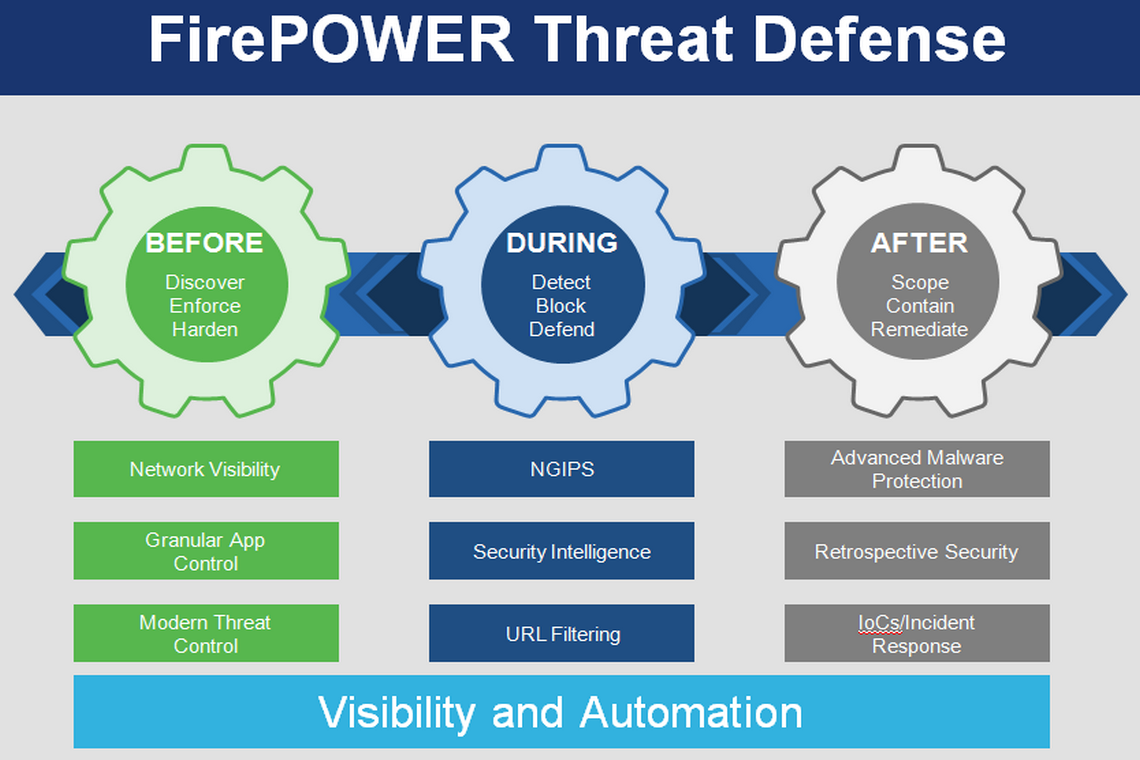
Now is the time to learn about the Cisco FTD. Before we dig into the software components and hardware platforms, let’s try to identify the difference between the FirePOWER Services and Firepower Threat Defense (FTD).
FirePOWER Service Versus Firepower Threat Defense (FTD)
As you might have guessed, FirePOWER Services refers to features that are similar to the pre-acquisition period software releases, such as Next-Generation Intrusion Prevention System Virtual (NGIPSv). In FTD, Cisco converges all the Sourcefire FirePOWER features, ASA firewall features, and some additional new features into one single unified software image.
Figure 1 illustrates the convergence of Cisco ASA software with Sourcefire FirePOWER software into the FTD code. Due to this convergence, FirePOWER Services no longer runs as a separate service module, which reduces overhead and increases efficiency.
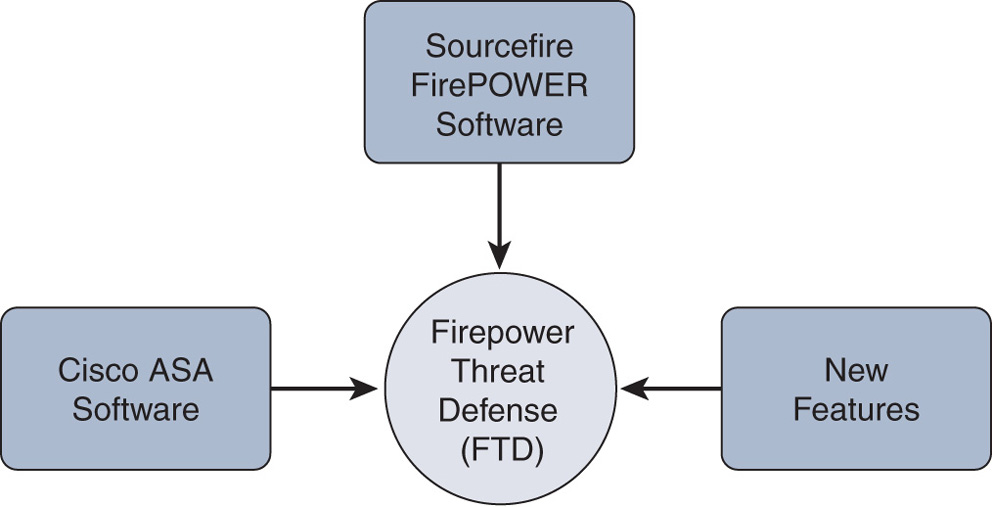
Figure 1 Logical Representation of the FTD Software
Note
This book is written based on Firepower Version 6.1 running on FTD. Although this book uses the ASA 5500-X Series hardware, managed using the Firepower Management Center (FMC), you can still apply this knowledge on other platforms running Firepower technologies.
Firepower System Software Components
The Firepower System offers lot of security features. Unlike with traditional Cisco ASA firewall software, the security features of the Firepower System are delivered as multiple software components:
- Firepower core software: The core part of the software includes the Snort engine for intrusion detection and prevention, a web server for the graphical user interface (GUI), a database to store events, firmware for the hardware, and so on. The core software image for the Firepower System depends on the hardware platform you are using.
- Software patches and hotfixes: Cisco releases software patches periodically to address any security vulnerabilities and to fix any defects with the Firepower System. When an issue demands resolution earlier than a scheduled maintenance update, Cisco may release a hotfix for it, on case-by-case basis.
- Snort/Sourcefire rules: The Snort engine uses a special ruleset to detect and prevent intrusion attempts. Each rule considers certain conditions. When a packet goes through a sensor and matches a condition in a Snort rule, the Snort engine takes the appropriate action.
- Vulnerability database (VDB): A VDB stores vulnerability information and fingerprints of various applications, services, and operating systems (OSs). The Firepower System uses the fingerprints to discover the application, service, and OS running on a network host, and then it correlates the application and network discovery data with the vulnerability information on a VDB.
- Geolocation database (GeoDB): A GeoDB stores geographical information and associated IP addresses. For example, when the Firepower System displays an intrusion event in the GUI, you can view the name and flag of the country that originated that intrusion attempt. This information allows you to make decisions quickly, without performing reverse lookups for IP addresses.
Figure 2 illustrates the various software components installed on the Firepower System. All these software components are explained in my later blogs.
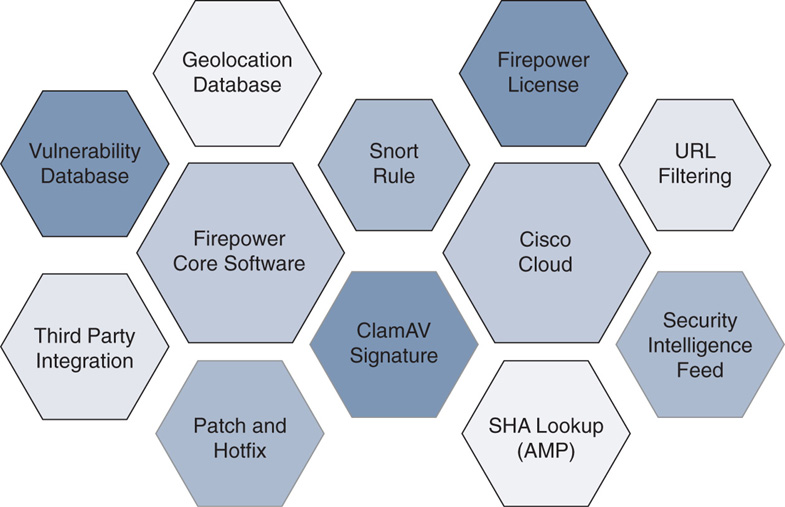
Figure 2 Firepower System Software Components
- URL filtering database: The Firepower System can categorize websites based on their targeted audiences or business purposes. To give you more granular control, the system also enables you to control access to a certain type of website, based on its reputation or known risk level. All this information is stored in the URL filtering database. Unlike with Firepower software components, any updates for the URL filtering database are provided directly through the Cisco cloud, so your FMC must be connected to the Internet.
- Security Intelligence Feed: Talos, the Cisco threat intelligence team, is continuously researching the Internet to identify potential malicious IP addresses, domain names, and URLs. For Firepower System users, Talos shares intelligence data through the Security Intelligence Feed. The FMC can download the feed directly from the cloud.
- Local malware detection: With a malware license, FTD can detect viruses in your files. This allows you to block the spread of malware across your network. FTD uses the ClamAV engine to analyze files locally. The FMC obtains the signatures of the latest viruses through the local malware detection updates.
- Integration: You can integrate the Firepower System with various products and technologies, such as Cisco Identity Services Engine (ISE), Microsoft Windows Active Directory Server, Event Streamer (eStreamer), and Syslog Server. This empowers you with unlimited opportunities to monitor and secure your network. (This book focuses on core Firepower technologies, and features related to integration are beyond the scope of this book. Please read the official Firepower user guide to learn more about integration.)
Firepower System Hardware Platforms
FTD Version 6.1 is available on a wide variety of hardware platforms. The internal architecture of each platform is different. There are, of course, differences in form factor, throughput, and price. Later in this book, you will learn more about the architectures and operations of the Firepower System.
Table 1 summarizes the hardware platforms (available as of this writing) that support FTD software. All of the following platforms support Version 6.1, except Firepower 2100 Series (Version 6.2.1 or greater) and Microsoft Azure (Version 6.2 or greater).
Table 1 Hardware Platforms That Support FTD Software
Hardware Category | Platform Name/Model Number |
| ASA5506-X, 5506H-X, 5506W-X, 5508-X, 5516-X, 5512-X, 5515-X, 5525-X, 5545-X, 5555-X |
| Firepower 2110, 2120, 2130, 2140 |
| Firepower 4110, 4120, 4140, 4150 |
| Firepower 9300 |
| VMWare ESXi/vSphere, Kernel-Based Virtual Machine (KVM), Amazon Web Services (AWS) Microsoft Azure |
Figure 3 illustrates the placement of various ASA and Firepower platforms in different types of networking environments. The throughput of appliances varies significantly depending on the number of enabled features, such as firewall (FW) only, firewall along with Cisco Application Visibility and Control (AVC), next-generation intrusion prevention system (NGIPS), URL filtering, SSL decryption, and so on.
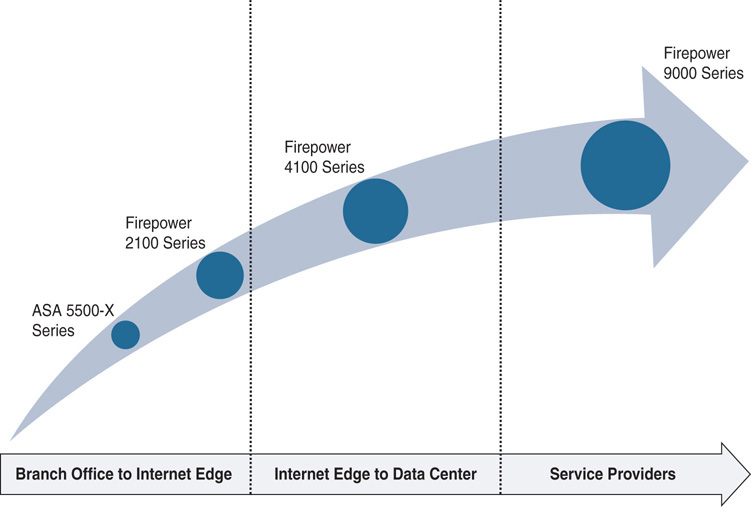
Figure 3 Placement of ASA and Firepower Appliances in Various Networking Environments with Different Needs
Note
To find out what hardware models support FTD and the throughput of each hardware model, please check the Cisco Firepower NGFW data sheet at cisco.com or contact your account representative.
Firepower Accessories
When you open a brand-new Firepower appliance box, you will find various accessories along with the actual appliance. The accessories are necessary to configure the initial setup and obtain a license. Figure 4 shows an example of the accessories that come with a Cisco ASA 5506-X appliance:
- The ASA 5506-X appliance (see #1 in Figure 4)
- A DB-9 to RJ-45 console cable (see #2)
- Envelope with the product activation key (PAK) (see #3)
- Power adapter (see #4)
- Power cord to connect with the power adapter (see #5)

Figure 4 Cisco ASA 5506-X Appliance Accessories Example
Note
The accessories in a box are subject to change, depending on various factors. In your box, you may receive more or fewer items than are shown in this example.
Tip
Read the Installation Guide for your appliance model (available at cisco.com) to learn how to install it into a rack and power it up.
Let's discuss now how to add security FTD features to your Cisco ASA equipment?