This article provides information and commands concerning the following topics:
Setting Passwords on a Switch
Setting passwords for switches is the same method as used for a router.
Switch2960(config)# enable password cisco | Sets the enable password to cisco |
Switch2960(config)# enable secret class | Sets the encrypted secret password to class |
Switch2960(config)# line console 0 | Enters line console mode |
Switch2960(config-line)# login | Enables password checking |
Switch2960(config-line)# password cisco | Sets the password to cisco |
Switch2960(config-line)# exit | Exits line console mode |
Switch2960(config)# line vty 0 15 | Enters line vty mode for all 16 virtual ports |
Switch2960(config-line)# login | Enables password checking |
Switch2960(config-line)# password cisco | Sets the password to cisco |
Switch2960(config-line)# exit | Exits line vty mode |
Switch2960(config)# |
Configuring Static MAC Addresses
Normally, switches learn of MAC addresses dynamically through the inspection of the source MAC address of incoming frames. These addresses then are placed in the Content Addressable Memory (CAM) table for future use. However, if required, you can manually add a MAC address to the CAM table—these are known as static MAC addresses. Static MAC addresses always overrule dynamic entries.
So why add static MAC addresses to the table? One reason could be to defeat a hacker who is trying to spoof a dynamically learned MAC address to change entries in the CAM table.
Switch2960(config)# mac address-table static aaaa.aaaa.aaaa vlan 1 interface fastethernet 0/1 | Sets a permanent address to port fastethernet 0/1 in VLAN 1 |
Switch2960(config)# no mac address-table static aaaa.aaaa.aaaa vlan 1 interface fastethernet 0/1 | Removes the permanent address to port fastethernet 0/1 in VLAN 1 |
Configuring Switch Port Security
Switch(config)# interface fastethernet 0/1 | Moves to interface configuration mode |
Switch(config-if)# switchport mode access | Sets the interface to access mode (as opposed to trunk mode) Note A port cannot be in the default Dynamic Trunking Protocol (DTP) dynamic mode for port security to be enabled. It must be in either access or trunk mode |
Switch(config-if)# switchport port-security | Enables port security on the interface |
Switch(config-if)# switchport port-security maximum 4 | Sets a maximum limit of four MAC addresses that will be allowed on this port Note The maximum number of secure MAC addresses that you can configure on a switch is set by the maximum number of available MAC addresses allowed in the system |
Switch(config-if)# switchport port-security mac-address 1234.5678.90ab | Sets a specific secure MAC address 1234.5678.90ab. You can add additional secure MAC addresses up to the maximum value configured |
Switch(config-if)# switchport port-security violation shutdown | Configures port security to shut down the interface if a security violation occurs Note In shutdown mode, the port is error-disabled, a log entry is made, and manual intervention or err-disable recovery must be used to reenable the interface |
Switch(config-if)# switchport port-security violation restrict | Configures port security to restrict mode if a security violation occurs Note In restrict mode, frames from a nonallowed address are dropped, and a log entry is made. The interface remains operational |
Switch(config-if)# switchport port-security violation protect | Configures port security to protect mode if a security violation occurs Note In protect mode, frames from a nonallowed address are dropped, but no log entry is made. The interface remains operational |
Configuring Sticky MAC Addresses
Sticky MAC addresses are a feature of port security. Sticky MAC addresses limit switch port access to a specific MAC address that can be dynamically learned, as opposed to a network administrator manually associating a MAC address with a specific switch port. These addresses are stored in the running configuration file. If this file is saved, the sticky MAC addresses do not have to be relearned when the switch is rebooted and thus provide a high level of switch port security.
Switch(config)# interface fastethernet 0/5 | Moves to interface configuration mode |
Switch(config-if)# switchport port-security mac-address sticky | Converts all dynamic port security learned MAC addresses to sticky secure MAC addresses |
Switch(config-if)# switchport port-security mac-address sticky vlan 10 voice | Converts all dynamic port security learned MAC addresses to sticky secure MAC addresses on voice VLAN 10 Note The voice keyword is available only if a voice VLAN is first configured on a port and if that port is not the access VLAN |
Verifying Switch Port Security
Switch# show port-security | Displays security information for all interfaces |
Switch# show port-security interface fastethernet 0/5 | Displays security information for interface fastethernet 0/5 |
Switch# show port-security address | Displays all secure MAC addresses configured on all switch interfaces |
Switch# show mac address-table [dynamic] | Displays the entire MAC address table Using the optional argument of dynamic will show only the dynamic addresses learned |
Switch# clear mac address-table dynamic | Deletes all dynamic MAC addresses |
Switch# clear mac address-table dynamic address aaaa.bbbb.cccc | Deletes the specified dynamic MAC address |
Switch# clear mac address-table dynamic interface fastethernet 0/5 | Deletes all dynamic MAC addresses on interface fastethernet 0/5 |
Switch# clear mac address-table dynamic vlan 10 | Deletes all dynamic MAC addresses on VLAN 10 |
Switch# clear mac address-table notification | Clears MAC notification global counters Note Beginning with Cisco IOS Release 12.1(11)EA1, the clear mac address-table command (no hyphen in mac address) replaces the clear mac-address-table command (with the hyphen in mac-address) |
Recovering Automatically from Error-Disabled Ports
You can also configure a switch to autorecover error-disabled ports after a specified amount of time. By default, the autorecover feature is disabled.
Switch(config)# errdisable recovery cause psecure-violation | Enables the timer to recover from a port security violation disabled state |
Switch(config)# errdisable recovery interval seconds | Specifies the time to recover from the error-disabled state. The range is 30 to 86,400 seconds. The default is 300 seconds Tip Disconnect the offending host; otherwise, the port remains disabled, and the violation counter is incremented |
Verifying Autorecovery of Error-Disabled Ports
Switch# show errdisable recovery | Displays error-disabled recovery timer information associated with each possible reason the switch could error-disable a port |
Switch# show interfaces status err-disabled | Displays interface status or a list of interfaces in error-disabled state |
Switch# clear errdisable interface interface-id vlan [vlan-list] | Reenables all or specified VLANs that were error-disabled on an interface |
Configuring DHCP Snooping
Dynamic Host Configuration Protocol (DHCP) snooping is a DHCP security feature that provides network security by filtering untrusted DHCP messages and by building and maintaining a DHCP snooping binding database, which is also referred to as a DHCP snooping binding table.
Switch(config)# ip dhcp snooping | Enables DHCP snooping globally Note If you enable DHCP snooping on a switch, the following DHCP relay agent commands are not available until snooping is disabled: Switch(config)# ip dhcp relay
information check
Switch(config)# ip dhcp relay
information policy {drop | keep | replace}
Switch(config)# ip dhcp relay
information trust-all
Switch(config-if)# ip dhcp relay
information trustedIf you enter these commands with DHCP snooping enabled, the switch returns an error message |
Switch(config)# ip dhcp snooping vlan 20 | Enables DHCP snooping on VLAN 20 |
Switch(config)# ip dhcp snooping vlan 10-35 | Enables DHCP snooping on VLANs 10 through 35 |
Switch(config)# ip dhcp snooping vlan 20 30 | Enables DHCP snooping on VLANs 20 through 30 |
Switch(config)# ip dhcp snooping vlan 10,12,14 | Enables DHCP snooping on VLANs 10, 12, and 14 |
Switch(config)# ip dhcp snooping vlan 10-12,14 | Enables DHCP snooping on VLANs 10 through 12 and VLAN 14 |
Switch(config)# ip dhcp snooping information option | Enables DHCP option 82 insertion Note DHCP address allocation is usually based on an IP address, either the gateway IP address or the incoming interface IP address. In some networks, you might need additional information to determine which IP address to allocate. By using the “relay agent information option” (option 82), the Cisco IOS relay agent can include additional information about itself when forwarding DHCP packets to a DHCP server. The relay agent will add the circuit identifier suboption and the remote ID suboption to the relay information option and forward this all to the DHCP server |
Switch(config)# interface fastethernet0/1 | Moves to interface configuration mode |
Switch(config-if)# switchport mode trunk | Forces the switch port to be a trunk |
Switch(config-if)# switchport trunk encapsulation dot1q | Creates an uplink trunk with 802.1Q encapsulation Note On newer switches that do not support ISL encapsulation, this command is not required (and may return an error) as there is no need to choose between ISL and dot1q |
Switch(config-if)# switchport trunk allowed vlan 10,20 | Selects VLANs that are allowed transport on the trunk |
Switch(config-if)# ip dhcp snooping trust | Configures the interface as trusted Note There must be at least one trusted interface when working with DHCP snooping. It is usually the port connected to the DHCP server or to uplink ports. By default, all ports are untrusted |
Switch(config-if)# ip dhcp snooping limit rate 75 | Configures the number of DHCP packets per second that an interface can receive Note The range of packets that can be received per second is 1 to 4,294,967,294. The default is no rate configured Tip Cisco recommends an untrusted rate limit of no more than 100 packets per second |
Switch(config-if)# exit | Returns to global configuration mode |
Switch(config)# ip dhcp snooping verify mac-address | Configures the switch to verify that the source MAC address in a DHCP packet that is received on an untrusted port matches the client hardware address in the packet |
Verifying DHCP Snooping
Switch# show ip dhcp snooping | Displays the DHCP snooping configuration for a switch |
Switch# show ip dhcp snooping binding | Displays only the dynamically configured bindings in the DHCP snooping binding database |
Switch# show ip source binding | Displays the dynamically and statically configured bindings |
Switch# show running-config | Displays the status of the insertion and removal of the DHCP option 82 field on all interfaces |
Configuring Dynamic ARP Inspection (DAI)
Dynamic ARP Inspection determines the validity of an ARP packet. This feature prevents attacks on the switch by not relaying invalid ARP requests and responses to other ports in the same VLAN.
Switch(config)# ip dhcp snooping | Enables DHCP snooping, globally |
Switch(config)# ip dhcp snooping vlan 10-20 | Enables DHCP snooping on VLANs 10 to 20 |
Switch(config)# ip arp inspection vlan 10-20 | Enables DAI on VLANs 10 to 20, inclusive |
Switch(config)# ip arp inspection validate src-mac | Configures DAI to drop ARP packets when the source MAC address in the body of the ARP packet does not match the source MAC address specified in the Ethernet header. This check is performed on both ARP requests and responses |
Switch(config)# ip arp inspection validate dst-mac | Configures DAI to drop ARP packets when the destination MAC address in the body of the ARP packet does not match the destination MAC address specified in the Ethernet header. This check is performed on both ARP requests and responses |
Switch(config)# ip arp inspection validate ip | Configures DAI to drop ARP packets that have invalid and unexpected IP addresses in the ARP body, such as 0.0.0.0, 255.255.255.255, or all IP multicast addresses. Sender IP addresses are checked in all ARP requests and responses, and target IP addresses are checked only in ARP responses |
Switch(config)# interface fastethernet0/24 | Moves to interface configuration mode |
Switch(config-if)# ip dhcp snooping trust | Configures the interface as trusted for DHCP snooping |
Switch(config-if)# ip arp inspection trust | Configures the connection between switches as trusted for DAI Note By default, all interfaces are untrusted |
Tip
It is generally advisable to configure all access switch ports as untrusted and to configure all uplink ports that are connected to other switches as trusted.
Verifying Dynamic ARP Inspection
Switch# show ip arp inspection interfaces | Verifies the dynamic ARP configuration |
Switch# show ip arp inspection vlan 10 | Verifies the dynamic ARP configuration for VLAN 10 |
Switch# show ip arp inspection statistics vlan 10 | Displays the dynamic ARP inspection statistics for VLAN 10 |
Configuration Example: Switch Security
Figure 20-1 shows the network topology for the secure configuration of a 2960 series switch using commands covered in this post. Commands from other articles are used as well.
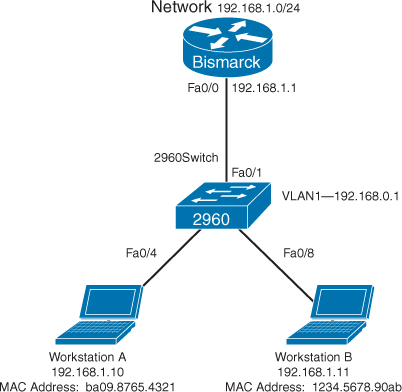
Figure 20-1 Network Topology for 2960 Series Switch Secure Configuration
Switch> enable | Enters privileged EXEC mode |
Switch# configure terminal | Enters global configuration mode |
Switch(config)# no ip domain-lookup | Turns off Domain Name System (DNS) queries so that spelling mistakes do not slow you down |
switch(config)# hostname Switch2960 | Sets the host name |
Switch2960(config)# enable secret cisco | Sets the encrypted secret password to cisco |
Switch2960(config)# line console 0 | Enters line console mode |
Switch2960(config-line)# logging synchronous | Appends commands to a new line; router information will not interrupt |
Switch2960(config-line)# login | Requires user to log in to console before use |
Switch2960(config-line)# password switch | Sets the password to switch |
Switch2960(config-line)# exec-timeout 0 0 | Prevents console from logging out due to lack of user input |
Switch2960(config-line)# exit | Moves back to global configuration mode |
Switch2960(config)# line vty 0 15 | Moves to configure all 16 vty ports at the same time |
Switch2960(config-line)# login | Requires user to log in to vty port before use |
Switch2960(config-line)# password class | Sets the password to class |
Switch2960(config-line)# exit | Moves back to global configuration mode |
Switch2960(config)# ip default-gateway 192.168.1.1 | Sets default gateway |
Switch2960(config)# interface vlan 1 | Moves to virtual interface VLAN 1 configuration mode |
Switch2960(config-if)# ip address 192.168.1.2 255.255.255.0 | Sets the IP address and netmask for switch |
Switch2960(config-if)# no shutdown | Turns the virtual interface on |
Switch2960(config-if)# interface fastethernet 0/1 | Moves to interface configuration mode for fastethernet 0/1 |
Switch2960(config-if)# description Link to Bismarck Router | Sets a local description |
Switch2960(config-if)# interface fastethernet 0/4 | Moves to interface configuration mode for fastethernet 0/4 |
Switch2960(config-if)# description Link to Workstation A | Sets a local description |
Switch2960(config-if)# switchport mode access | Sets the interface to access mode |
Switch2960(config-if)# switchport port-security | Activates port security |
Switch(config-if)# switchport port-security mac-address sticky | Converts all dynamic port security learned MAC addresses to sticky secure MAC addresses |
Switch2960(config-if)# switchport port-security maximum 1 | Allows only one MAC address in the MAC table. This is the default number and not a required command, shown here for a visual reminder |
Switch2960(config-if)# switchport port-security violation shutdown | Turns off port if more than one MAC address is reported. This is the default action and not a required command, shown here for a visual reminder |
Switch2960(config-if)# interface fastethernet 0/8 | Moves to interface configuration mode for fastethernet 0/8 |
Switch2960(config-if)# description Link to Workstation B | Sets a local description |
Switch2960(config-if)# switchport mode access | Sets the interface to access mode |
Switch2960(config-if)# switchport port-security mac-address 1234.5678.90ab | Sets a specific secure MAC address 1234.5678.90ab. You can add additional secure MAC addresses up to the maximum value configured |
Switch2960(config-if)# switchport port-security maximum 1 | Allows only one MAC address in the MAC table. This is the default number and not a required command, shown here for a visual reminder |
Switch2960(config-if)# switchport port-security violation shutdown | Turns off port if more than one MAC address is reported. This is the default action and not a required command, shown here for a visual reminder |
Switch2960(config-if)# exit | Returns to global configuration mode |
Switch2960(config)# exit | Returns to privileged EXEC mode |
Switch2960# copy running-config startup-config | Saves the configuration to NVRAM |
Switch2960# |

