We continue the story about Selinux. In the previous article, we revealed some of the onsite jobs for beginners. Now we will consider SELinux modes.
SELinux is either enabled or disabled in a system. When enabled, it operates in either of the following modes:
- Enforcing: SELinux effectively monitors and controls security policies. In RHEL/CentOS, this mode is enabled by default.
- Permissive: Security policies are actively monitored without enforcing access control. Policy violations are logged in /var/log/messages.
When SELinux is disabled, security policies are neither monitored nor enforced.
The following command retrieves the current status of SELinux on the system:
sestatusThe output is as follows:
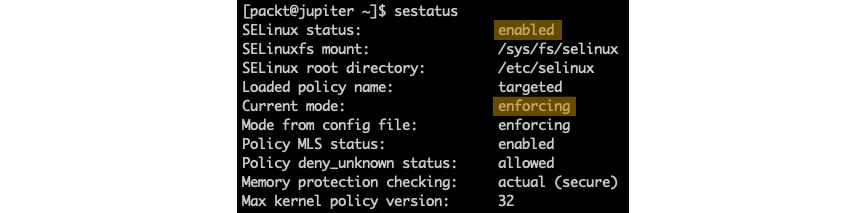
Figure 12 – Getting the current status of SELinux
When SELinux is enabled, the following command retrieves the current mode:
getenforceIn permissive mode, we get the following output:
![]()
Figure 13 – Getting the current mode of SELinux
To change from enforcing to permissive mode, we can run the following command:
sudo setenforce 0The getenforce command will display Permissive in this case. To switch back into enforcing mode, we can run the following command:
sudo setenforce 1The SELinux mode can also be set by editing the SELINUX value in /etc/selinux/config. The possible values are documented in the configuration file.
Important note
Manually editing the SELinux configuration file requires a system reboot for the changes to take effect.
With SELinux enabled, a system administrator may choose between the following SELinux policy levels by modifying the SELINUXTYPE value in /etc/selinux/config: targeted, minimum, and mls. The corresponding values are documented in the configuration file.
Important note
The default SELinux policy setting is targeted, and it's generally recommended not to change this setting, except for mls.
With the targeted policy in place, only processes that are specifically configured to use SELinux security policies run in a confined (or restricted) domain. Such processes usually include system daemons (such as dhcpd and sshd) and well-known server applications (such as Apache and PostgreSQL). All other (non-targeted) processes run unrestricted and are usually labeled with the unconfined_t domain type.
To completely disable SELinux, we can edit the /etc/selinux/config file using a text editor of our choice (such as sudo nano /etc/selinux/config) and make the following change:
SELINUX=disabledAlternatively, we can run the following command to change the SELinux mode from enforcing to disabled:
sudo sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/configWe can retrieve the current configuration with the following command:
cat /etc/selinux/configWith SELinux disabled, we get the following output:
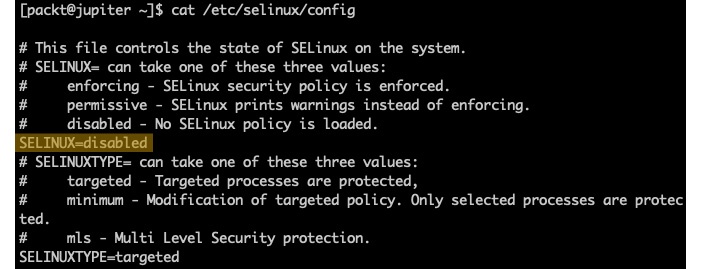
Figure 14 – Disabling SELinux
We need to reboot the system for the changes to take effect:
sudo systemctl rebootNext, let's examine how access control decisions are made by introducing SELinux contexts.

