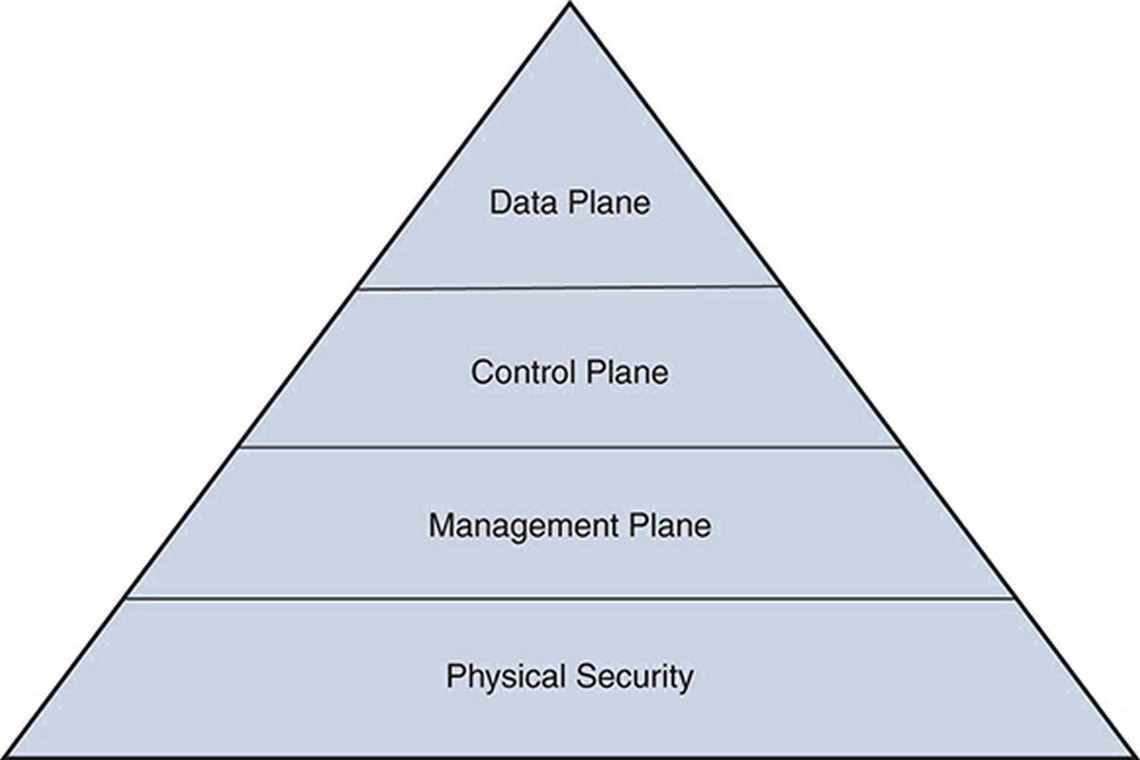
We did not leave the world of security for the astral planes, and neither did we switch to the flying kind. The planes we discuss here are the three that exist on a network device: the management, control, and data planes.
Any functions related to managing a device, such as configuring it, happen in the management plane. Access to this plane requires use of various protocols, such as SSH, Telnet, SNMP, and SFTP. This is the most important plane in terms of securing a device because any breach on this plane will allow access to all data flowing through the device and even the ability to reroute traffic.
In the control plane, the device discovers its environment and builds the foundation to do its job. For example, a router uses routing protocols in the control plane to learn about the various routes. Routes allow a router to do its primary job—route packets. A switch uses protocols such as VTP and STP to learn about various paths, and that allows it to switch traffic. If the protocols in the control plane are not secured, a malicious actor may be able to inject rogue control packets and influence the path of the packets. For example, if your routing protocols are not secure, then it is possible to inject rogue routes, causing data to flow to a different device. This technique is often used in man- in-the-middle (MITM) attacks.
The data plane, also called the forwarding plane, is where the actual data flows. When a router receives a packet to route or a switch receives a frame to switch, it does so on the data plane. Information learned in the control plane facilitates the functions of the data plane. Typically, this is where most of the network security controls are focused. Packet filtering, protocol validation, segmentation, malicious traffic detection, distributed denial-of-service (DDoS) protection, and other security measures are utilized in this plane.
In addition to the three planes, the physical security of a device itself is important. After all, the security in the software does not matter if the hardware is compromised. While it is the responsibility of the vendor - Cisco in this case - to ensure that a device is not tampered with between manufacturing and your doorstep, it is your responsibility to ensure that the devices are kept in a secure location where unauthorized access can be prevented.
The three planes and physical security can be visualized as the pyramid shown in Figure 1, where compromise on one layer will affect all the layers above it.
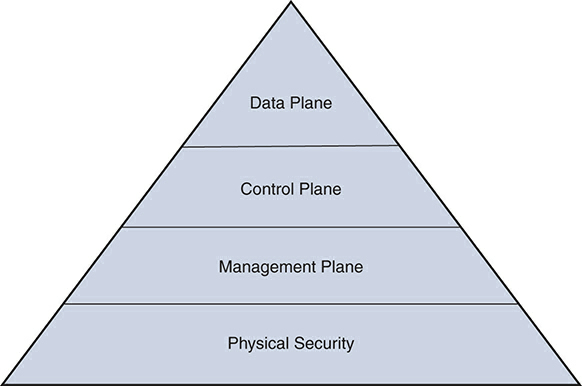
Figure 1 The Pyramid of Planes