So far in my blog, we have discussed how to assess risks and create a security policy, taking into consideration regulatory requirements. Creating a security policy is just the first step in securing your organization. A security policy only indicates the requirements of the business and its management. It needs to be implemented to be of any use!
How do you effectively implement a security policy? The answer is by using security models. While it is not necessary to use a defined model, using one will make the implementation and auditing more effective and uniform. A security model helps convert requirements of a policy into a set of rules and regulations.
You should know some of the most common and widely accepted security models:
- Bell–LaPadula Model: This state machine model was introduced to enforce access control in government and military applications. This model is primarily focused on the confidentiality of data and controlled access to classified information.
- Biba Model: This lattice-based model was developed to focus on integrity of data. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not write to objects in a higher level.
- Clark–Wilson Model: This model was developed to address integrity for commercial activities (whereas the previous two models were developed for government and military applications). The model uses a system of a three-part relationship known as a triple, consisting of a subject, a program, and an object. Within this relationship, a subject can only access an object through a program.
- Lattice-Based Model: This mandatory access control (MAC)–based model uses a lattice to define the levels of security for subjects and objects. A subject can only access objects that have a security level equal to or lower than its own security level.
A lot of these security models were developed a long time ago for specific use cases. Changing network and security requirements have created a need for better and simpler security models. To address this need, Cisco created the SAFE architecture and model.
Cisco SAFE
The Cisco SAFE model provides a method for analyzing threats, risks, and policies across an organization and implementing controls. It takes into account that all organizations are not the same by providing a modular structure that can be customized for any type and size of organization.
The model divides the network into logical areas called places in the network (PINs), as shown in Figure 1.
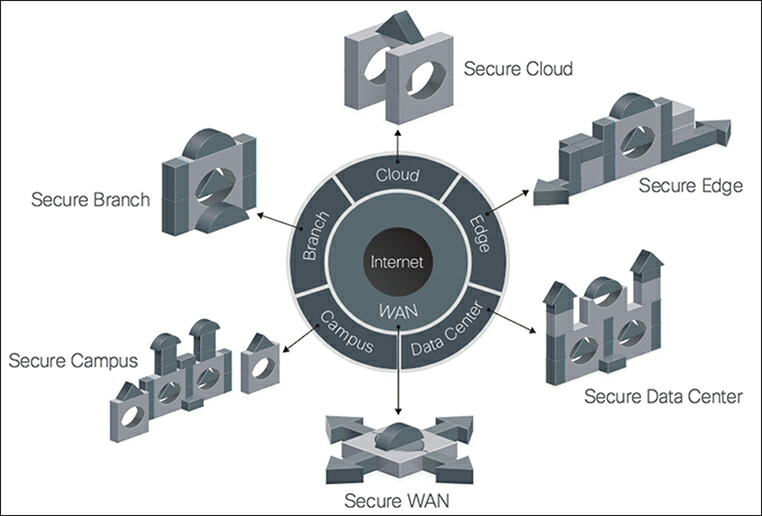
Figure 1 Places in the Network, as Defined by Cisco SAFE
Each PIN is evaluated across a set of six operational functions, called secure domains, as shown in in Figure 2.
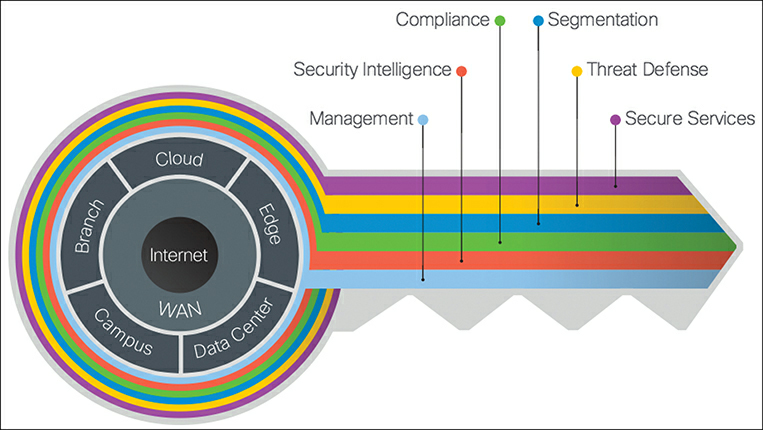
Figure 2 The Key to SAFE
Based on the PINs and security domain approach, the SAFE model defines a three-phased approach for building security in the network:
- Capability phase: Using business goals, security policy, risks, and threats in each PIN, justify which security capabilities are required.
- Architecture phase: Using the justified capabilities, arrange them in a logical architecture.
- Design phase: Using the architecture, create a design that is complete with a product list, configuration, services, and cost.
SAFE PINs
As mentioned earlier, the SAFE model divides the network into six logical areas, or PINs. It is not necessary for each organization to have every area, but the model is designed to be modular. You can remove PINs that do not exist in your network. Each PIN represents the infrastructure commonly deployed in these areas, such as routers, switches, firewalls, and so on.
Each of the six PINs has a typical profile and associated threats:
- Branch: Branches present a unique security challenge due to their smaller size and larger number of locations. Providing a level of security in branches that is comparable to the campus or data center level is cost-prohibitive. This leaves branches more vulnerable and makes them prime targets. Typical threats in branches include point-of-sale malware, wireless infrastructure exploits such as rogue access points, and exploitation of trust.
- Campus: Campuses contain a large number and many types of users, including employees and guests. Traditional methods of segmentation are used at the campus level, with very few internal security controls. There is often a lack of access control in the wired network within the campus. All these factors combined make campuses easy targets for phishing, malware propagation, unauthorized network access, and botnet infestation.
- Data center: Data centers contain the crown jewels of an organization and hence get the biggest share of the security budget. However, the data center is also the most targeted PIN. In addition, data centers contain thousands of servers, segmented by application type, data classification, and so on, using traditional manual methods. Managing and auditing these segmentations is increasingly difficult. Typical threats seen in data centers are data exfiltration, malware propagation, and advanced persistent threats.
- Edge: The edge is the most critical PIN in terms of business importance as well as security risk. It is the primary ingress and egress point for traffic to and from the Internet. It is very susceptible to DDoS attacks. Other threats that are common to this PIN are data exfiltration, MITM attacks, and web server vulnerability exploits.
- Cloud: The cloud is the new frontier, bringing high risk along with high cost savings. Security in the cloud is dictated by service-level agreements (SLAs) with the provider and requires regular audits and risk assessments. The primary threats in this PIN are DDoS and MITM attacks, loss of access, data loss, and web server vulnerabilities.
- Wide area network: The WAN connects other PINs, such as branch, campus, and data centers, together. In a large organization with hundreds of locations, managing security and quality of service (QoS) on the WAN is challenging. Typical threats seen in this PIN are malware propagation, exploitation of trust, unauthorized network access, and MITM attacks.
Secure Domains
The SAFE model divides the operational side of security into six secure domains. Every secure domain applies to each PIN in an organization. An evaluation of all the secure domains across each PIN provides a list of security capabilities that are required. These are the six secure domains defined by Cisco SAFE:
- Management: This refers to centralized management of devices and systems. Centralized management is essential for consistent security policy, vulnerability patching, security application updates, and alerting. Some of the capabilities within this domain are policy configuration, time synchronization, patch management, and logging/reporting.
- Security intelligence: This refers to global aggregation of emerging malware and threats to provide timely detection. A threat protection infrastructure is as good as the security intelligence it receives. The infrastructure needs to be able to dynamically enforce new policies as threats emerge and change. Some of the capabilities within this domain are threat intelligence, malware sandboxing, and posture assessment.
- Compliance: This refers to controls that need to exist to satisfy internal and external compliance requirements, such as those for HIPAA and PCI DSS. Some of the capabilities in this domain include virtual private networks, firewalls, and intrusion prevention systems.
- Segmentation: This refers to segmentation of data, devices, and users. Traditional manual segmentation uses a combination of network addressing, VLANs, and access lists. Advanced segmentation is identity-aware, dynamic, and automated.
- Threat defense: This refers to the ability to detect, prevent, eliminate, or contain cyber threats. Modern-day threats are evasive and persistent. Correlation of network traffic telemetry, contextual information, and reputation data is required to detect such threats. Some of the capabilities in this domain include intrusion prevention, flow and behavior analysis, antimalware systems, and application visibility controls.
- Secure services: This refers to technologies such as access control, VPNs, and secure email services. This domain adds security on top of services that are inherently insecure, such as email, network access, and collaboration. Some of the capabilities in this domain include email security, web application firewalls, and VPNs.
Attack Continuum
Cisco SAFE defines three phases of an attack—before, during, and after—together called the attack continuum:
- Before: In this phase of the continuum, you need to know the asset being protected and the threat against which you are defending. Establishing policies and implementing prevention to reduce risk belong in this phase.
- During: This phase defines the abilities and actions that are required when an attack gets through. Analysis and incident response are some of the typical activities associated with this phase.
- After: This phase defines the ability to detect, contain, and remediate after an attack. If an attack was successful, any lessons learned need to be incorporated into the existing security solution.
For each secure domain in every PIN, you need to define and implement capabilities such that each phase of the continuum is covered.
Figure 3 shows various Cisco products and solutions that work across the attack continuum.
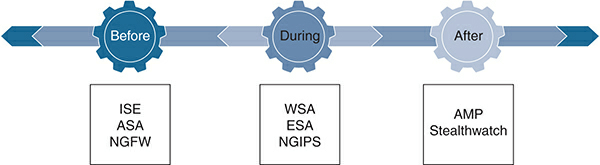
Figure 3 Cisco Products and Solutions Across the Attack Continuum



